Features | Open Source | Releases | Docs | Try us free | Blog | Product
How to use OAuth2 Tokens in Platform?
EN | ES
Onesait Platform is ready to work with OAuth2 authentication. Following we'll see the OAuth2 Token management flow.
1. OAuth2 Realm configuration parameters
When creating or Updating a Realm, there are two parameters to be configured associated to the OAuth Tokens:
- KEY (Secret): key that will be used for clients's authentication..
- TOKEN VALIDITY TIME (S): configurable duration (in seconds) in which the generated token will be valid.
They are non-obligatory attributes. In case of not informing them, they will take default values (onesaitplatform and 43200 (12 hours)).
2. Token Generation
There is an endpoint that allows OAuth2 token generation.
The URL is like this: https://lab.onesaitplatform.com/oauth-server/oauth/token
It's a POST request, and it must include:
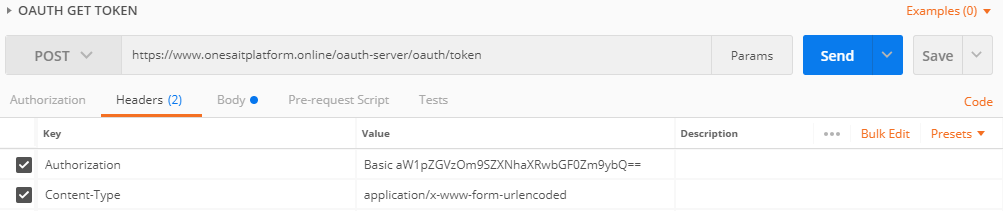
- Headers:
- Authorization: (client:secret b64)
- Content-Type: application/x-www-form-urlencoded
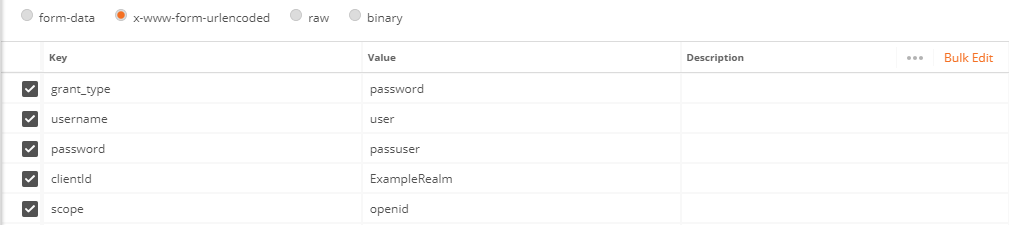
- Body:
- grant_type: password (User/Password request)
- username: user's Id
- password: user's password
- clientId: client's Id for Token use
- scope: Token scope
Using Postman to send this request, it will be something like this:
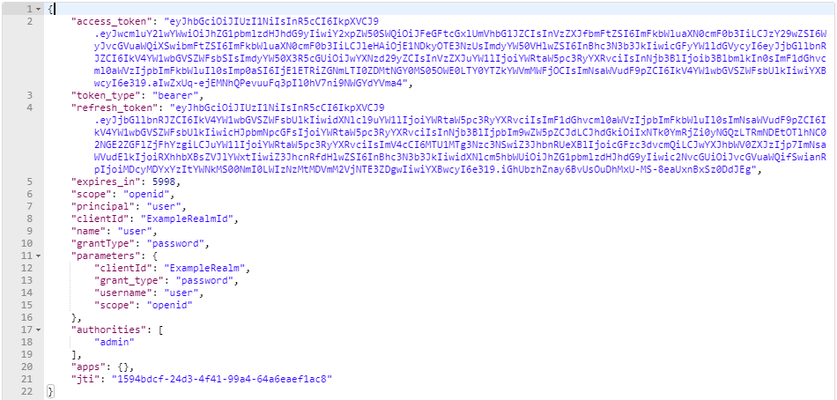
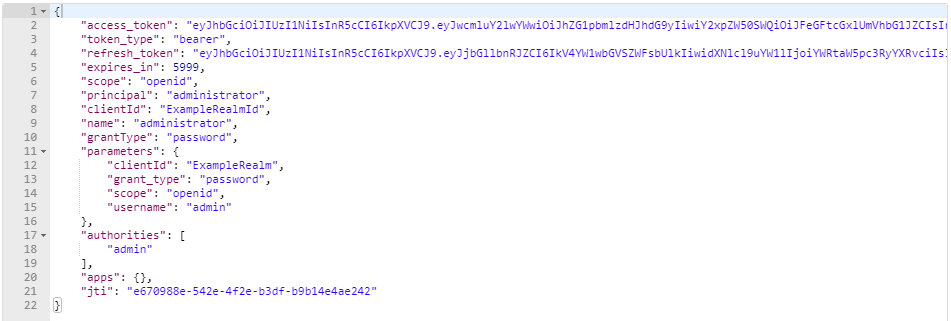
The response will be like this:
To Highlight:
- access_token: Access token
- refresh_token: Refresh Token (one use)
- expires_in: Remaining validity time (seconds)
- authorities: Realms' roles asigned to the user
3. Chek Token
Service that verifies the validity of a token. The endpoint will be like this: https://lab.onesaitplatform.com/oauth-server/openplatform-oauth/check_token
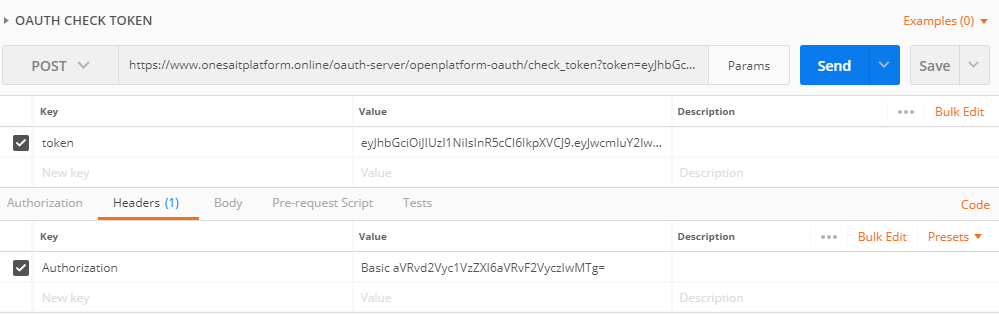
The POST request must include:
- Headers:
- Authorization: (client:secret b64)
- Parameter:
- token: token to validate
Using postman:
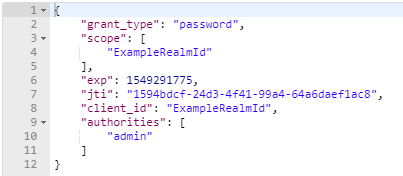
If the token is valid, a response will be obtained in the form:
To Highlight:
- exp: Expiration date
- client_id: client for which the token was generated
- authorities: Realm's Roles to which the token's user belongs
4. Refresh Token
Service that regenerates the token in order to obtain another one. The endpoint is like this: https://lab.onesaitplatform.com/oauth-server/oauth/token
(the same as for getting a new token, changes the grant-type).
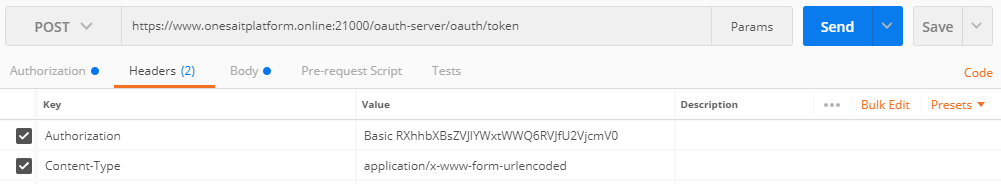
The POST request must include:
- Headers:
- Authorization: (client:secret b64)
- Content-Type: application/x-www-form-urlencoded
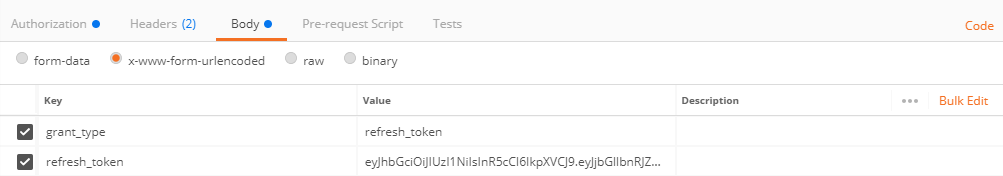
- Body:
- grant_type: refresh_token (for token refresh)
- refresh_token: refresh token obtained when generating the token)
Using Postman:
The result is the same as for a get token request:
The refresh token is one-use token. After regenerating the token, a new refresh token will be provided.
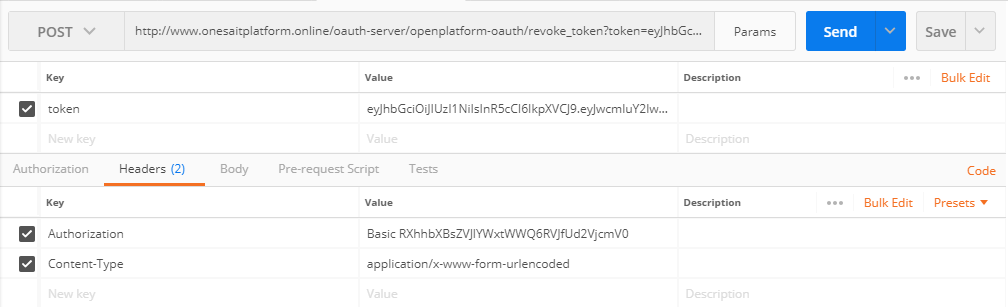
5. Revoke Token
As an addional service, a revoke token service has been included. It allows to disable (revoke) an existing access token associated to an user.
The endpoint is like this: https://lab.onesaitplatform.com/oauth-server/openplatform-oauth/revoke_token
The POST request must include:
Headers:
- Authorization: (cliente:secret en b64)
- Content-Type: application/x-www-form-urlencoded
Query Param:
- token: (token to revoke)
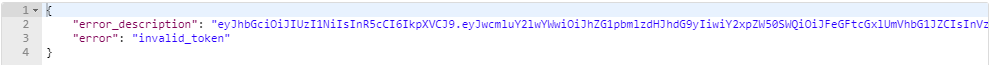
In Postman:
The result will indicate that the token is not longer valid:
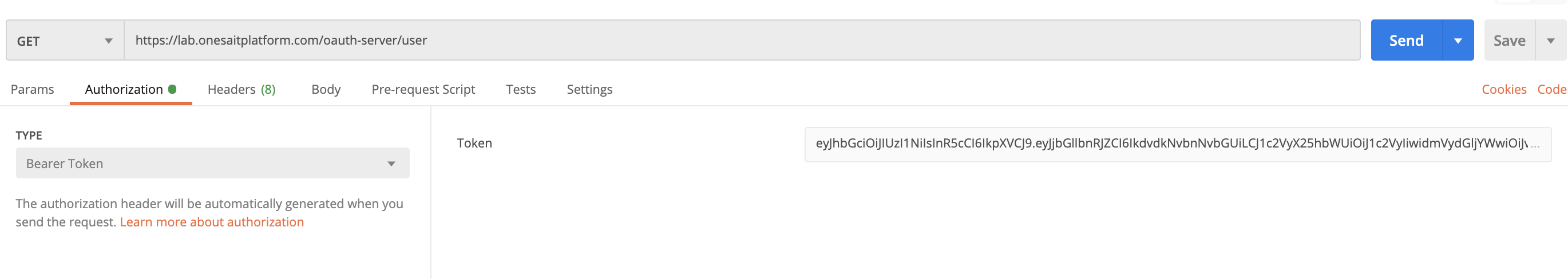
6. User info endpoints
An endpoint to retrieve user claims. The url is like this: https://lab.onesaitplatform.com/oauth-server/user
The POST request must include:
Headers:
- Authorization: Bearer {jwt}
In postman: